 In the 1990’s and early 2000’s when a new company started out and bandwidth was precious, most businesses implemented an on premise directory server with either Novell or Microsoft Active Directory (AD). The Small Business edition of Active Directory was a cost effective option to start out. Active Directory worked well for on premise Windows PCs but did not help much with road warriors. A single on premise AD server was a big single point of failure, adding high availability and remote replication to an AD server is a non-trivial task that added cost and complexity to an early stage company.
In the 1990’s and early 2000’s when a new company started out and bandwidth was precious, most businesses implemented an on premise directory server with either Novell or Microsoft Active Directory (AD). The Small Business edition of Active Directory was a cost effective option to start out. Active Directory worked well for on premise Windows PCs but did not help much with road warriors. A single on premise AD server was a big single point of failure, adding high availability and remote replication to an AD server is a non-trivial task that added cost and complexity to an early stage company.
Over the years, as Mac workstations and laptops became more popular in the enterprise especially small software development companies, AD was not a good solution for managing OSX based devices. There has not been an outstanding solution for managing Macs. Apple made small inroads to managing Macs with OSX Server and Open Directory, but that initiative never really gained traction. Google introduced the Munki/Simian based toolset in 2013 to manage Macs at scale.
Today’s healthcare companies must have the ability to deploy and monitor the security and configuration of their Mac Workstations, as well as Windows and Linux based workstations and computers. It is no longer an option to deploy unmanaged Mac OSX devices and hope that believing “Macs don’t get viruses” is sufficient to pass a customer security review.
In April 2014, JumpCloud introduced their Directory as a Service (DaaS) tools. The JumpCloud DaaS product is a cloud based directory that supports Windows, Linux and Mac workstations and Servers. JumpCloud DaaS works well with Software as a Service (SaaS) vendors by supporting LDAP authentication as well as SAML SSO. Many SaaS vendors now have advanced user provisioning APIs (eg Google G-Suite) that allow users to be provisioned in G-Suite via the JumpCloud portal.
 For users, having one login to access all of their SaaS tools and a single multi factor authentication option, the experience of on boarding and accessing SaaS tools is simplified. There is one set of password complexity rules for JumpCloud instead of different complexity rules for multiple SaaS applications. If the organization wants to enable multi-factor authentication (MFA), just turn it on in JumpCloud and all SaaS will have MFA enabled.
For users, having one login to access all of their SaaS tools and a single multi factor authentication option, the experience of on boarding and accessing SaaS tools is simplified. There is one set of password complexity rules for JumpCloud instead of different complexity rules for multiple SaaS applications. If the organization wants to enable multi-factor authentication (MFA), just turn it on in JumpCloud and all SaaS will have MFA enabled.
For IT, managing user add/change/deletes and access rights is simplified by having a directory in the cloud. Also having tools to deploy scripts to Windows, Linux and Mac devices from a single portal is an incredible efficiency booster. JumpCloud also supports the deployment of SSH public keys providing an elegant tool set to manage SSH public keys on servers, solving a real world problem of deploying SSH keys for development and DevOps teams. Now it is easy to disable SSH password logins and use only SSH public/private key pairs. A user’s public key will be pushed to any system that you enable for the user in the JumpCloud portal. No more need to write scripts that use ssh-copy-id.
For DevOps, not having to allocate technical resources to manage Active Directory and Federation services is an order of magnitude simplification of the task of managing directory servers as well as cost.
JumpCloud is easy to setup, by creating a free 10 day account here. JumpCloud is free for up to 10 users forever, perfect for DevOps teams to practice with their own small domains. If you have more than 10 users, the trial is free for 10 days. Until this month, there was a $100/month minimum so the 11th user was expensive. However, JumpCloud eliminated this minimum charge as of August 23, 2018.
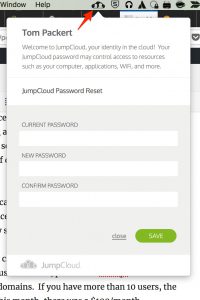 Anyone who has managed Macs at any scale without a directory server knows the pain of user management. The JumpCloud system and the JumpCloud agent makes user Mac user management simple and almost magical. Just this month the JumpCloud agent for Mac gained the Menu Bar option to better manage Mac local passwords with JumpCloud. Click the Menu Bar option on your mac and you can quickly update the local Mac Password and the JumpCloud Password.
Anyone who has managed Macs at any scale without a directory server knows the pain of user management. The JumpCloud system and the JumpCloud agent makes user Mac user management simple and almost magical. Just this month the JumpCloud agent for Mac gained the Menu Bar option to better manage Mac local passwords with JumpCloud. Click the Menu Bar option on your mac and you can quickly update the local Mac Password and the JumpCloud Password.
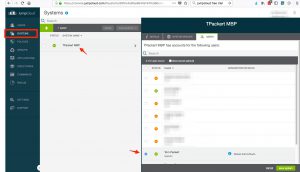 How does the Jumpcloud agent sync users between JumpCloud and the Mac local users? It is amazingly simple, the account name field in the Mac’s local Users Advanced Options setting must match the account name in the JumpCloud directory. Adding a user to a system is as simple as ticking a check box next to the user’s name on the system in the JumpCloud portal and within 60 seconds the user will be created on the local Mac.
How does the Jumpcloud agent sync users between JumpCloud and the Mac local users? It is amazingly simple, the account name field in the Mac’s local Users Advanced Options setting must match the account name in the JumpCloud directory. Adding a user to a system is as simple as ticking a check box next to the user’s name on the system in the JumpCloud portal and within 60 seconds the user will be created on the local Mac.
JumpCloud also uses a service account on the Mac to be able to manage the FileVault II whole drive encryption. Note: It is a good practice to add a System Admin account to every mac so that there is a common system administrator user on all macs.
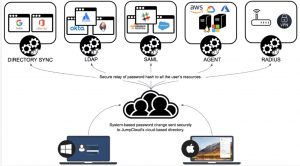 JumpCloud supports the following user management features.
JumpCloud supports the following user management features.
Directory Sync with Office 365 and Google G-Suite. When you create a new user in JumpCloud tick on the G-Suite or Office 365 options for the user, the user will be automatically provisioned in G-Suite or Office 365.
Generalized LDAP authentication when a device like a NAS needs to have LDAP authentication. The users are not synced, the LDAP authentication happens at runtime/login time.
SAML Single Sign On Authentication for SaaS providers for web based authentication. There are two types of SAML SSO. For AWS IAM authentication, the configuration supports just in time provisioning. This means that the user does NOT need to be manually created in AWS IAM first. The other SAML SSO is a manual provisioning (eg box.com) where the user is manually created in Box but the SAML SSO is used for authentication when the user wants to login to box.com
The JumpCloud agent allows users to be managed on local workstations and servers by way of the agent that syncs the user credentials. One elegant aspect of the JumpCloud agent is that the credentials are pushed locally to the devices/servers. If you are an admin on 100 AWS EC2 instances, when you change your password, the updated password will be automatically pushed to all 100 instances. There is no need for EC2 instances to have LDAP authentication configured for runtime authentication.
JumpCloud also supports Radius as a Service so that the small offices can authenticate their user access to a directory rather than the typical post it notes and whiteboards used for sharing WIFI WPA keys. With JumpCloud any size office can have directory based WIFI access controls.
