If you have Jumpcloud installed as your Directory as a Service, patching Zoom’s latest ZeroDay Vulnerability is pretty straighforward for office and remote workers.
Here is a link to an article on the NTLM Vulnerability https://www.bleepingcomputer.com/news/security/zoom-lets-attackers-steal-windows-credentials-run-programs-via-unc-links/
Jumpcloud has a feature called “Commands”. For Windows machines, the commands can be CMD or Powershell. LInux and Mac commands are also supports but those commands are bash scripts. In order to patch all the Windows machines.
I wrote a short Powershell script based on the advice in the Bleeping Computer article. The deployed the script to all of the computers with Jumpcloud and was done. This method can be used to add Registry Values to any group of Windows systems whether they are on premise and in a domain or remote.
1 – Login to JumpCloud Admin portal
2 – Click on Commands on the Left portal
3 – Click on + icon to add a command
4 – Give the Command a Name “ZoomPatch”
5 – Click on PowerShell
6 – Paste the code below into the command field
7 – Select Command Runners and select the Admin account to run command
8 – Select Systems and then select all systems to apply this patch to
9 – Click Save
10 – The select the ZoomPatch Command and Click the Run Now button
11 – Check the results in the results space at the bottom of the commands page
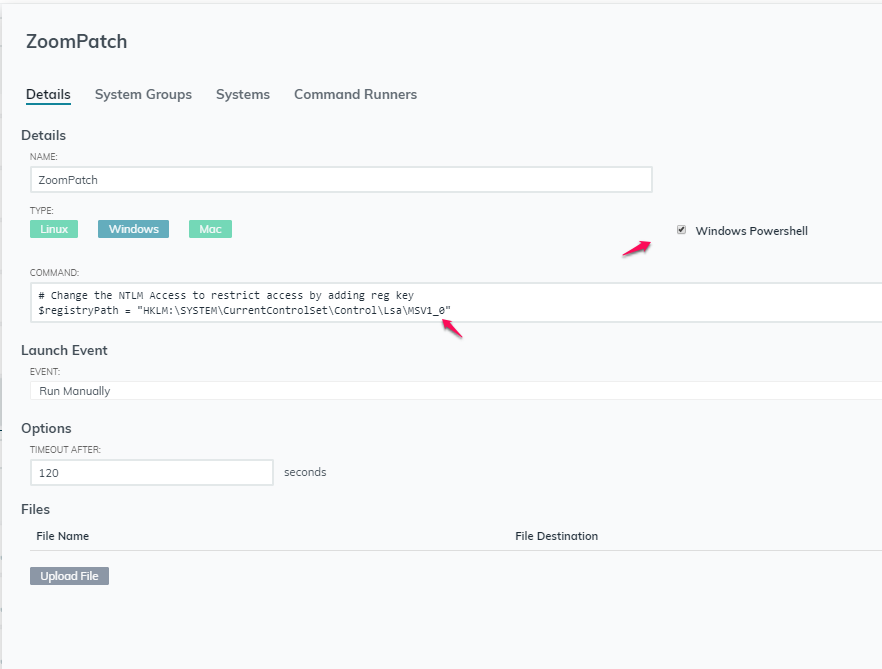
Change the NTLM Access to restrict access by adding reg key
$registryPath = "HKLM:\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0" $Name = "RestrictSendingNTLMTraffic" $value = 2 New-ItemProperty -Path $registryPath -Name $Name -value $value -PropertyType "DWord"
