Phishing attacks are extremely sophisticated today. One of the problems facing small businesses is the lack of robust IT security and support systems and the cleverness of the attackers. Employees at small companies need to be exceptionally aware of targeted phishing attacks which could lead to significant financial losses. This article will describe a simple five minute step that will mitigate one form of these clever spear phishing attacks.
One form of the phishing attack I have seen three times in recent years uses a slightly misspelled variation of the domain name. I have seen very convincing emails appearing to be from a CFO to a controller, including email trails from the CEO to wire money quickly to some account. The emails included instructions that the paperwork will follow. The perpetrators even follow up insistently via email continuing to impersonate the CFO as to whether the wire has been sent. It takes quite an astute recipient to look for subtle clues that the email is not real. The human tendency is to please an insistent boss and to follow the instructions to wire the money quickly. Imagine how an employee might feel, after wiring a potentially devastating amount money to an account because of being duped by a cleverly crafted email.
One occurrence of this scam was enabled by the popular VistaPrint.com website. The perpetrator registered a domain name similar to ours with only two letters transposed. The names of the officers were real and the email trail back and forth looked genuine. Clearly, there was a lot of time put into this effort to defraud us. VistaPrint.com does not require a credit card for a free 30 day trial so there was no risk of being caught. Today, I was still able to sign up for the same typo domain name on VistaPrint without a credit card.
Fortunately, our controller was pretty sharp and the email raised her suspicions, a good trait for a controller. Using the “Show Original” option on google mail I was able to determine how the email was delivered. The originating domain was legitimate with DKIM and SPF validations passing. The only clue was the inspection of the domain name and the IP address was not ours which lead me to a closer inspection of the domain name. It was right there in plain sight, two letters transposed.
I thought a lot on how to prevent this from occurring in the future. It is common practice to post your company leadership on your website. Also, companies make their internal management structure visible on LinkedIn. It was probably these public sources of information that gave the fraudsters the names of the people to include on the emails. I thought about posting ‘honey pot’ officers on the website and LInkedin and set filters when these users receive emails. But I nixed that because it would cause too much confusion to our legitimate customers and partners.
Next, I thought about why would we be targeted? It turns out this is pretty easy answer. If you issue press releases, as a startup, about receiving substantial investments, you will become a prime target. Not only because you have money in the bank, but startups tend to have less formal procedures and are more chaotic. Startups also tend not to have fulltime IT security staff that can react quickly to threats. The fraudsters invest in these schemes because it pays and there is little chance of being caught. When I contacted VistaPrint.com’s legal department, they let me know that their own executive team had been duped into wiring money. Fortunately, they were able to recall the wire transfer, but it was a close call.
So what other ways have I thought about on how to prevent this. One idea was to add a word or picture of the day to the email signatures. This could easily be done with the BetterCloud signature tools that schedule signature updates for Gmail signatures. There are two problems with this. One, the users would still need to be vigilant, less so than catching two transposed letters but still vigilant. The other is that Gmail signatures only work on the web client and not mobile devices. Any email sent from a mobile device will be missing the word or picture of the day.
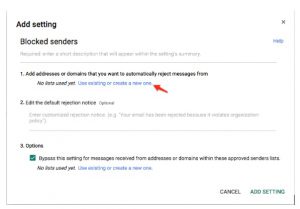
My final solution which I believe should be a new best practice is to add a list misspellings of the company’s domain name to the Gmail blocked senders list. The blocked senders list is a feature of the paid Google Apps for Work. It is not available to the free legacy Google Apps accounts. I used the SEOTools Typo generator tool (link here) to create a list of typos to add to the blocked senders list. I entered my company name and was given a list of likely names. You can manually add other names where 1s are swapped with l’s and O’s with 0’s, B’s and 8’s etc. Updating your company’s blocked senders list is a simple five minute task that could potentially save your company a lot of pain and financial loss in the future.
Here is a link to a document on how to add blocked senders to your Google Apps account. The instructions are likely to change so it is better to refer to Google’s documentation for this process. You will need to be an admin on the Google Apps domain. Click on the gear and select “Admin this Domain”. Select APPS >> Google APPS >> Settings for GMAIL >> Advanced Settings. Scroll down to the SPAM section and select ADD ANOTHER. Then select “Use Existing or Create a new one”, then Create, give the list a name like typos_20151103 and paste the generated typo list into the box. The UI is not quite intuitive, as with many things Google Admin related, but it works. You can also edit a rejection message to the blocked senders list.
The only caveat to this technique is that if you have want to receive email from a legitimate company that is only one letter away from your domain name you will need to update the blocked senders list. Most of the time this will be very unlikely.
Here is a link to a useful white paper about many more types of bank fraud schemes. The key take away, is to understand that busy entrepreneurs who issue press releases about investment funding will attract scammers and your finance staff should to trained to look for these types of attempts to steal your money.
Note: This blocked senders feature is also very useful to block emails from competitors that may have hired your staff or you are hiring their staff.
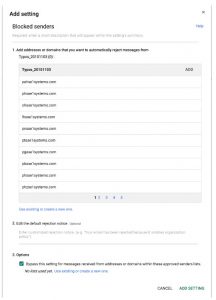
List of typos generated by the SEO Typo tool
- pahse1systems.com
- phsae1systems.com
- ohase1systems.com
- lhase1systems.com
- pnase1systems.com
- ptase1systems.com
- pgase1systems.com
- pbase1systems.com
- phsse1systems.com
- phzse1systems.com
- phqse1systems.com
- phaee1systems.com
- phaae1systems.com
- phade1systems.com
- phawe1systems.com
- phase1eystems.com
- phase1aystems.com
- phase1dystems.com
- phase1wystems.com
- phase1ststems.com
- phase1sustems.com
- phase1shstems.com
- phase1syetems.com
- phase1syatems.com
- phase1sydtems.com
- phase1sywtems.com
- phase1sysrems.com
- phase1sysgems.com
- phase1sysyems.com
- phase1systens.com
- phase1systeks.com
- phase1systejs.com
- phase1systeme.com
- phase1systema.com
- phase1systemd.com
- phase1systemw.com
- phase1systems.dom
- phase1systems.vom
- phase1systems.xom
- phase1systems.cim
- phase1systems.clm
- phase1systems.cpm
- phase1systems.con
- phase1systems.cok
- phase1systems.coj
